TL;DR for decision-makers
Integrating Brightree with other systems via MuleSoft is powerful, but handling patient health data (PHI) brings HIPAA obligations. Success comes from three layers:
- Legal contracts (BAA)
- Secure architecture (encryption, access controls, logging)
- Operational safeguards (testing, monitoring, incident response)
This guide shows you how to approach it strategically, without drowning in technical minutiae.
Why HIPAA compliance matters for integrations
HIPAA governs how PHI is stored, transmitted, and accessed. Non-compliance risks fines, patient trust, and partnerships. Decision-makers must balance innovation with legal accountability and audit-readiness.
When integrating Brightree with MuleSoft’s Anypoint Platform, new PHI pathways are created that must be secured, documented, and monitored to HIPAA standards.
Brightree in a nutshell
Brightree provides a cloud-based platform for post-acute healthcare operations. It offers APIs for patient records, claims, orders, and billing. These APIs allow connections to external systems, but since PHI flows through them, you must ensure controls at every hop.
Brightree patient API call & response:
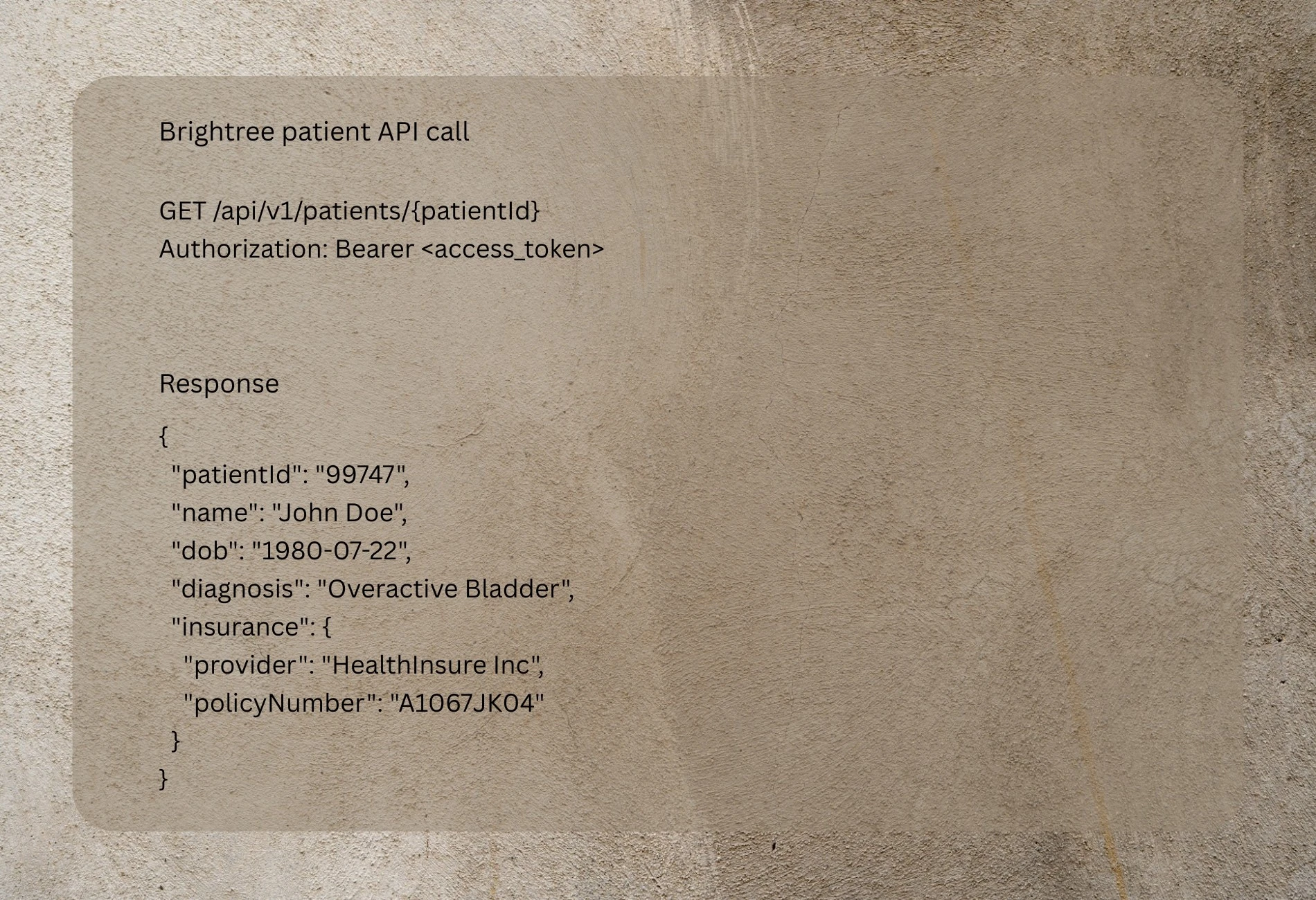
This illustrates how direct PHI (name, DOB, diagnosis) is exposed. The integration layer must treat this as highly sensitive.
MuleSoft’s role in HIPAA-compliant integrations
- Anypoint Security: tokenization, data masking, TLS enforcement.
- X12/EDI HIPAA connectors: standardized claim and eligibility transactions.
- RBAC (role-based access control) and identity federation.
- Audit logging and monitoring, integration with SIEM tools.
These features reduce custom build risk and provide a compliance-ready backbone.
Step-by-step guide to HIPAA-compliant Brightree ↔ MuleSoft integration
Step 1: Secure the legal foundation
- Ensure Business Associate Agreements (BAAs) are signed with Brightree and MuleSoft/Salesforce.
- Verify scope of services, including whether testing environments are covered.
Step 2: Map PHI data flows
- Identify which Brightree APIs expose PHI and which downstream systems require it.
- Apply the minimum necessary rule: strip or tokenize unnecessary identifiers.
Step 3: Architect integration with compliance in mind
Two common patterns:
- Direct API mediation: Brightree API → MuleSoft API gateway → downstream EHR or billing.
- Event-driven with tokenization: Brightree events → MuleSoft queue → transform & mask identifiers → downstream analytics.
Illustrative MuleSoft flows:

This shows how MuleSoft can intercept and mask PHI before data moves downstream.
Step 4: Enforce access & encryption
- TLS 1.2+ for all traffic
- Manage keys via a dedicated KMS
- OAuth2/OpenID Connect for API access
- RBAC for role-based PHI access
Step 5: Lock down non-production environments
- Never load real PHI into dev or QA.
- Use synthetic datasets mimicking Brightree structures.
Step 6: Build logging & audit trails
- Log every PHI access and transformation.
- Store logs in an immutable or tamper-evident system.
- Feed logs into a SIEM to detect suspicious patterns.
Step 7: Test, validate & audit
- Run penetration tests and vulnerability scans.
- Validate HIPAA EDI/X12 formats with MuleSoft connectors.
- Perform regular risk assessments and maintain audit evidence.
Step 8: Plan for incidents
- Document breach response: roles, containment, notifications to HHS and patients.
- Test incident plan annually.
Compliance checklist
- Signed BAAs with Brightree and MuleSoft
- Documented PHI data flow maps
- Encryption in transit & at rest (TLS 1.2+, KMS)
- OAuth2 + RBAC for access management
- No PHI in non-production
- Immutable logs + SIEM monitoring
- Annual risk assessment + breach response plan
Conclusion
If you’re evaluating Brightree + MuleSoft integration but need clarity on HIPAA compliance checkpoints, contact our team to discuss tailored architecture recommendations.
Developer Tips & Insights